BVSEC
Analysis and detection of vulnerabilities and malicious code

Benefits
- Binary-only approach, no access to source code
- Unified vulnerability & malware detection
- Full automation and industrial scalability
- Automatic execution with every build or delivery
Key words
- Vulnerability
- CI/CD
- Cybersecurity
- Malware
Laboratory
- VERIMAG
Institutions
- CNRS
- GRENOBLE INP-UGA
- UGA
Linksium Continuum
- Maturation
Context
Software security still relies mainly on source code analysis, even though a growing proportion of critical software is distributed solely in binary form: third-party libraries, proprietary components, legacy software and firmware. At the same time, the software chain is becoming more complex and exposed, with CI/CD automation, increasing dependencies and stricter regulatory requirements (SBOM, auditability, compliance). Existing tools remain ineffective on pure binary code, often cumbersome, fragmented and poorly integrated with DevSecOps practices.
Technology
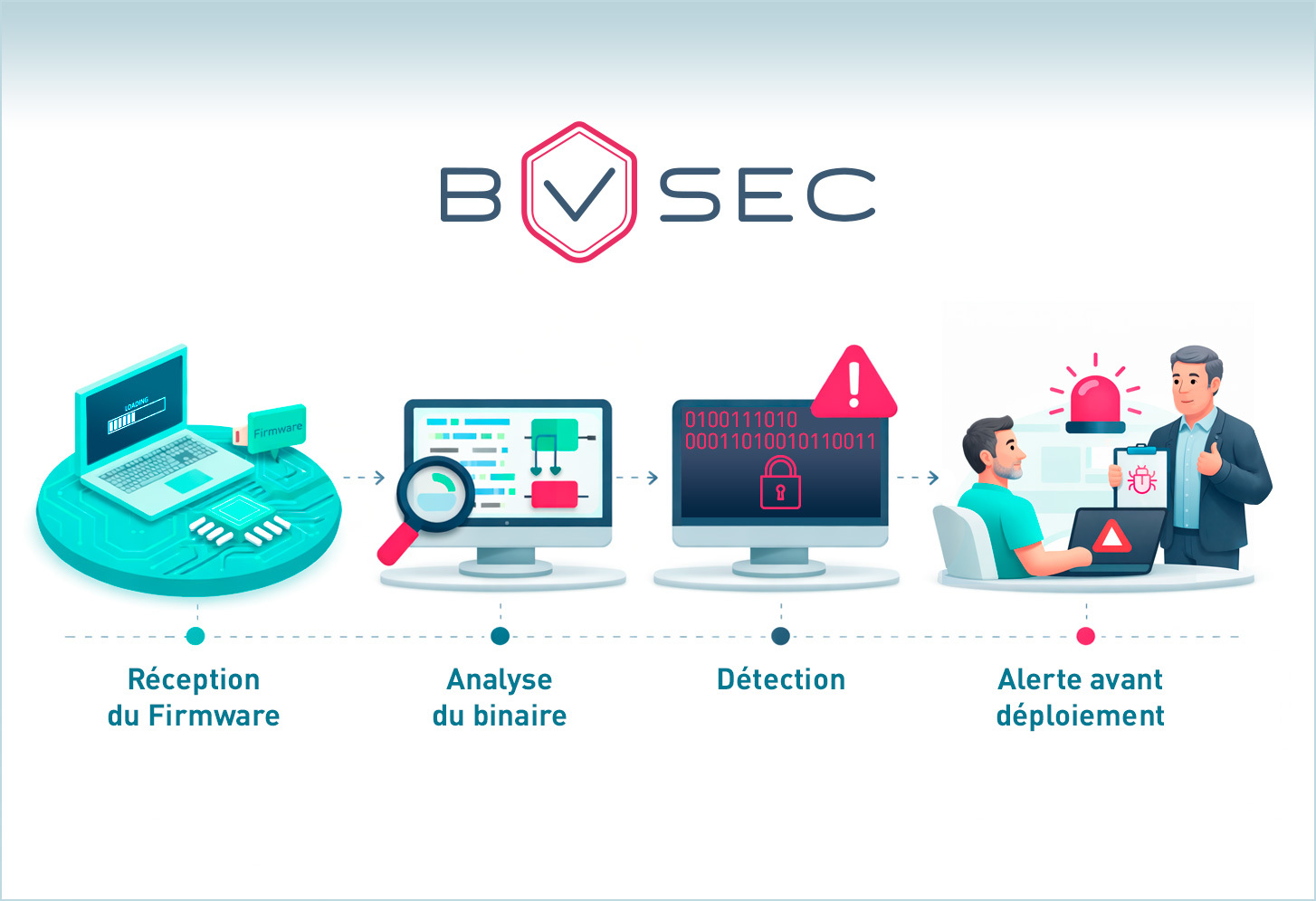
BVSec is a platform for automatically detecting vulnerabilities and malware directly from binaries, without access to the source code. It analyses the structure and semantics of the binary, extracts patterns and behaviours, and then applies unified AI capable of identifying exploitable flaws and malicious behaviours. The results are explainable, facilitating security analysis and compliance.
Advantages
BVSec stands out thanks to its binary-only approach, unified vulnerability/malware detection and complete automation. The platform is designed to be scalable, run automatically with each build or delivery, and enable early detection of risks before production, while producing actionable insights for auditing and compliance.
State of progress
BVSec is currently at TRL 3–4 maturity, with validated concepts, functional prototypes and initial experimental validations on real binaries. The path is clearly defined towards an industrial TRL 5–6 MVP, including platform hardening, full CI/CD integration and gradual scaling up.
Applications
The main use cases cover software supply chain security, DevSecOps integration in CI/CD, auditing proprietary software without source code, analysing firmware and embedded systems, and large-scale binary analysis services for MSSPs and SOCs.

Featured articles
 SERIAL TECH TRANSFR
SERIAL TECH TRANSFR
1, 2 and 3 startups for Nora Dempsey, National Medal of Innovation 2021
Nora Dempsey is one of the four winners of National Medal for Innovation 2021 awarded by CNRS. Nora Dempsey, born in Ireland, has gained an international recognition for her research in Grenoble on...
Read the article PORTRAIT
PORTRAIT
Amiral Technologies, la startup IA grenobloise spécialisée dans les solutions de maintenance prédictive, intègre Station F
An ambitious promise: to invent a zero-defect and zero-downtime future for industry. Amiral Technologies, a startup co-founded and boosted by Linksium, based on the technological prowess of the Gre...
Read the article